Access Management in an organization is the virtue of how well the organization function when it comes to authorization of assets to users. The concerning aspect of unauthorized access is eliminated with effective access management in any organization. In this article, we will learn about the objective, process, and values of Access Management.
ITIL Access Management
Access is the extent of a service’s or asset’s functionality that a particular user is authorized to use. ITIL access management is the process responsible for allowing only authorized users to access certain assets and IT services while preventing unauthorized users from accessing them.
ITIL Access Management Objective
The main objective of ITIL access management is to safeguard the data from being accessed by unauthorized users. This is extremely vital for an organization as critical data falling into the wrong hands could cause irreversible damage to the company.
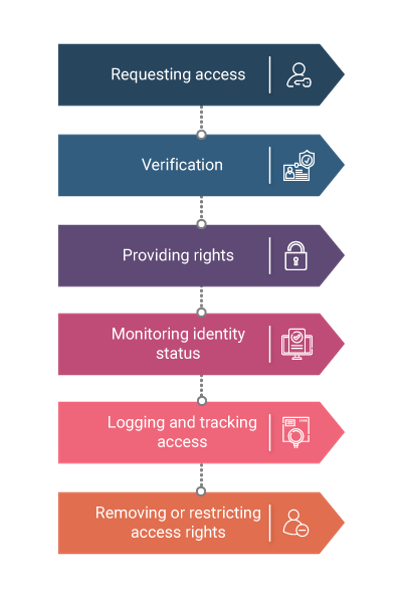
ITIL Access Management Process
Requesting Access
The first step is to request access to a particular IT service by sending one of the following types of requests.
-
- A Standard request was sent directly from the Human Resources department.
- A request for change is sent from the change management process.
- A service request was raised from the service desk.
- An auto-provisioning request where smaller requests are automatically handled.
Verification
It is the duty of access management to verify the identity of the user making the request and the legitimacy of the request being made.
Providing Rights
After the identity of the user has been verified, the access management grants him the right to access a particular IT service as per the regulations defined during the ITIL Service Strategy. If undefined, the access management grants the user, rights to access the service after sending requests to the respective departments in question and receiving approval.
Monitoring Identity Status
In a large organization, there is a constant change of employees in a particular position or requesting IT service access. It is the duty of the access management to keep track of all the access rights granted to the various employees and update them once the relevant employees are no longer in that position.
Logging and Tracking Access
Access management also has to keep constant tabs on the IT service users who have been granted access. All the activities of service operation processes should be monitored to ensure that only the users with the relevant clearance and authorization are accessing a particular IT service. They should also define parameters that make it easy to detect intrusions into the system by unauthorized users, excess incorrect login attempts, and unusual activities.
Removing or Restricting Access Rights
The access rights of a user have to be monitored so that when the role of the user changes over a period of time and he no longer needs access to a previously needed IT service, the authorization for access should be revoked. Depending on the present status of the user, their access needs to be restricted or terminated accordingly.
Value of ITIL Access Management to Business
Access Management provides the following values to business
- It ensures that by controlling the access to different IT services, the confidentiality of information will be maintained.
- Ensures that the employees have only the required level of access to complete their jobs effectively.
- Reduces the possibility of an error being induced in the use of a crucial service by not allowing unskilled users to access them.
- It provides a means to audit the IT services and trace any misuse of the services.
- Ensures that access to the service to a particular user can be withdrawn when needed to comply with security requirements.
Conclusion
Access management is thus successful in safeguarding the data from being accessed by unauthorized users, which is extremely vital for an organization. This prevents critical data from falling into the wrong hands and prevents damage to the company. Give yourself a chance to grow in your Service Management career with the ITIL 4 Foundation certification training, and gain useful skills and best practices.
Know more about Service Management best practices through Invensis Learning’s IT Service Management certification training on ITIL V4 Training and Certification, SIAM Foundation, SIAM professional, VeriSM, etc.